Exploiting Application-Level Profile Semantics (APLS)
TL;DR
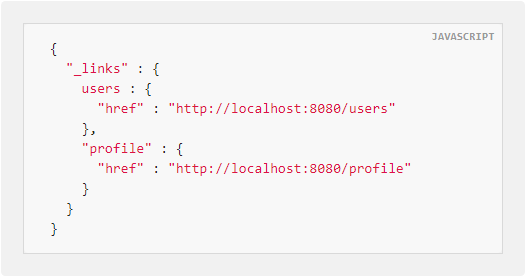
Application-Level Profile Semantics (APLS) from Spring may be unknown for you, as it was for me until a few days ago when I found an APLS definition exposed on a web application. I almost missed those Critical bugs. If that’s the case, this post will explain to you how to understand what APLS is, how it works, how to understand these definitions, and how it can be abused.
…My first International talk – Recon & BlackHat

Security Conferences
I don’t usually write this kind of posts, but after giving my first international talk in a Security Conference (YEAHHH!) I would like to share my experience with you since this can be useful to everyone who hasn’t talked yet against a big audience as it could be Recon in Montreal or any other big conference.
My idea is to show you my experience with the goal of motivating you all. Giving a talk in a security conference is usually one important and huge step into your professional life, and I’ve enjoyed it so much that I want to encourage you all to do the same.
…Reversing XignCode3 Driver – Part 4.2 – Verifying windows version
Quick post to analyze a particular function where the XC3 Driver manages the different version of Windows and bring support to each of them.
Introduction
As you may know, on windows the offsets inside of different kernel structure may change from one version to the next one.
Critical kernel structures like EPROCESS, KTHREAD, etc, have a lot of information on their attributes. Anti-Cheats usually access that information to manually check information about processes, system and memory by their own, without the need of using the windows API.
…Bypassing Anti-Cheats – Part 1 – Exploiting Razer Synapse Driver
This is another series of blog posts where I will be explaining some interesting facts that I implemented for “AntiCheat-Testing-Framework”, which can be found on my Github. In this case, I will show you how much we can learn from a <10 lines exploit 🙂
What we will go through?
- Learn how to write an exploit for a vulnerable driver.
- Learn to identify the vulnerable IOCTL by reversing the .sys file
- Learn about the technical background of the vulnerability
- Identify the Device Name of the Driver
- Identify input/output buffer format and size
- Successfully exploit the vulnerability
AntiCheat-Testing-Framework
Being this the first post of the series, I need to introduce what AntiCheat-Testing-Framework is:
…Reversing XignCode3 Driver – Part 4.1 – Registering Notify and Callback Routines
First of all, if you are just jumping into this topic I recommend you reading this post from GuidedHacking that will give you a lot of information about this Anti-Cheat.
I thought I could cover all about Notify and Callback routines on one post, my bad. To keep it short, I’m dividing this part of the analysis on multiple posts.
As a short summary I leave you here the link to the previous posts:
…